Levelling up Microsoft Defender
Introduction
Microsoft Defender is commonplace in smaller organisations without AV centralisation, or those that may not wish to purchase enterprise AV subscriptions. However, what is not commonplace is moving beyond the default configuration to provide enhanced protection for endpoints.
Microsoft provides a variety of configuration options via Group Policy, InTune, PowerShell or SCCM which enhance Defender’s detection capabilities; pushing Defender to the forefront of modern threat detection. This article serves to summarise information provided through Microsoft’s latest security baseline for Windows 10 and Windows Server 2016, along with collating information from other security professionals and official Microsoft documentation in an easily digestible format.
We will cover delivering cloud protection, enhancing cloud-based protection, blocking potentially unwanted programs, and will take a look at Defender’s attack surface reduction rules. This post will cover Group Policy-based deployment, as well as the available PowerShell commandlets, though as mentioned above, InTune and SCCM deployments are available.
Enable and enhance cloud-based protection
Microsoft Defender’s cloud-based protection “uses distributed resources and machine learning to deliver protection to your endpoints at a rate that is far faster than traditional Security intelligence updates“. This ensures that endpoints take advantage of stronger protection in addition to standard real-time protection.
Group Policy
As with all enhancements discussed herein, Group Policy can be configured to enable/enhance cloud protection. This is achieved through the following path – Computer configuration -> Administrative templates -> Windows Components -> Microsoft Defender Antivirus -> MAPS.
The “Join Microsoft MAPS” setting should be configured as Enabled with either Basic or Advanced membership (the distinction does not matter on Windows 10 systems). The “Send file samples when further analysis is required” setting should be set to either Send safe samples or Send all samples, depending on your individual requirements.
In summary, the MAPS settings should be configured like so –
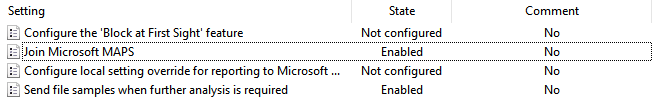
These settings can also be defined on local instances, via SCCM or through Microsoft InTune as described in the documentation available at this link.
PowerShell
Cloud-based protection can be enabled through PowerShell on either a standalone machine, or potentially on many machines through remoting or otherwise. Thankfully, Microsoft has made Defender’s PowerShell commandlets incredibly easy to use, with only two commands required to enable cloud-based protection –
Note: These commands must all be ran as an Administrator.
Set-MpPreference -MAPSReporting Advanced
Set-MpPreference -SubmitSamplesConsent AlwaysPrompt
Once enabled, you can confirm whether or not MAPS is enabled on a device by extracting the MAPSReporting setting from the malware protection preferences like so –
$(Get-MpPreference).MAPSReporting
A result of 0 indicates that MAPS reporting is not enabled, and either 1 or 2 means that cloud-based protection should be enabled.
Enhancing cloud-based protection
So now we’ve enabled cloud-based protection along with sample submission, but what else can we configure? Well, we can also enable real-time cloud-based detection for suspicious activities, define the cloud protection blocking level and cloud-based scanning for suspicious files.
Group Policy
Real-time cloud-based detection can be enabled through Computer configuration -> Administrative templates -> Windows Components -> Microsoft Defender Antivirus -> MAPS, by setting the “Configure the ‘Block at First Sight’ feature” setting to Enabled. This requires the following prerequisites –
- MAPS -> “Join Microsoft MAPS” set to Enabled
- MAPS -> “Send file samples when further analysis is required” set to Send safe samples or Send all samples
- Real-time Protection -> “Scan all downloaded files and attachments” must be enabled
- Real-time Protection -> Do not enable “Turn off real-time protection”
The other two settings are configurable through Computer configuration -> Administrative templates -> Windows Components -> Microsoft Defender Antivirus -> MpEngine. The current Microsoft security baseline does not recommend adjusting the cloud protection level, and the Microsoft docs warn against setting a higher protection level as it may lead to increased false positives. If desired, you can adjust this setting to either High, High+ or Zero Tolerance (with the risk of false positives naturally increasing at each step change).
As described in the “Configure extended cloud check” help section, the default cloud check timeout is 10 seconds. This can be increased to allow for extended checking – for example, adjusting the setting to 50 seconds will result in an addition 50 seconds of checks alongside the default 10 seconds, i.e. 60 seconds in total.
PowerShell
Note: These commands must all be ran as an Administrator.
Microsoft’s docs on Set-MpPreference seem a little outdated, so at first glance, it does not appear to be possible to adjust either the extended cloud check duration through PowerShell commandlets. But by reviewing the output of Get-MpPreference, extended cloud check and adjusting the cloud protection level is possible like so –
Set-MpPreference -CloudBlockLevel High
High can be substituted with either HighPlus or ZeroTolerance to match the potential options mentioned above.
Block at First Sight can be enabled via the Set-MpPreference commandlet like so –
Set-MpPreference -DisableBlockAtFirstSeen $False
Finally, the cloud-based extended check can be adjusted through the CloudExtendedCheck property –
Set-MpPreference -CloudExtendedTimeout 50
Troubleshooting cloud-based protection
With all these settings enabled, it’s important that we confirm we’re actually receiving the requested protection. Thankfully, Microsoft has well-documented information around confirming and troubleshooting connectivity issues.
Once you’ve deployed the Group Policy changes and allowed them to refresh on a test PC, launch Command Prompt as an administrator (must be an elevated prompt or else you’ll receive a 80070005 error).
From Command Prompt, run the following – "%ProgramFiles%\Windows Defender\MpCmdRun.exe" -validatemapsconnection. You should receive a successful response like so –
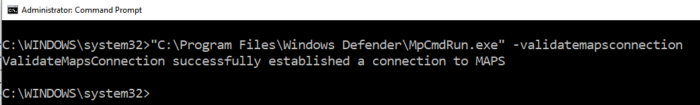
If you do receive an error when running the above command, check out Microsoft’s docs page on troubleshooting cloud-based protection – it includes required URLs, and a sample file which should be detected if cloud-based settings are enabled.
Blocking potentially unwanted programs
Group Policy
For whatever reason, Microsoft Defender doesn’t enable PUP protection by default – a feature offered by most other anti-virus applications. This feature can be enabled through Group Policy via the following path – Computer configuration -> Administrative templates -> Windows Components -> Microsoft Defender Antivirus through the setting “Configure detection for potentially unwanted applications“.
This setting can be set to either Audit or Block. Block will naturally block potentially unwanted programs, whereas Audit will log an event to the event log under event ID 1160 through Application and Services Logs\Microsoft\Windows\Microsoft Defender Antivirus\Operational.
This setting can also be set up through InTune, and is enabled by default through SCCM.
PowerShell
Note: These commands must all be ran as an Administrator.
Potentially Unwanted Programs can be blocked through PowerShell through the following commandlet –
Set-MpPreference -PUAProtection 1
Again, you can easily verify whether or not this setting is enabled by checking the result from Get-MpPreference for the PUAProtection property
$(Get-MpPreference).PUAProtection
Attack surface reductions
Group Policy
Microsoft offers several attack surface reduction rules to prevent common malware behaviours. Unfortunately, these are not the most user-friendly in their naming convention as they use GUIDs (though a mapping from GUID to a friendly description is available here). It is not exactly clear if all of these reduction rules will continue to remain available to users without Defender ATP, however I will include them below anyway.
Attack surface reduction rules can be enabled via Computer configuration -> Administrative templates -> Windows Components -> Microsoft Defender Antivirus -> Windows Defender Exploit Guard -> Attack Surface Reduction.
Microsoft’s security baseline recommends the following GUIDs set to Block (I have included friendly description mappings from the link above) –
| GUID | Friendly description |
| be9ba2d9-53ea-4cdc-84e5-9b1eeee46550 | Block executable content from email client and webmail |
| b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 | Block untrusted and unsigned processes that run from USB |
| 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 | Block credential stealing from the Windows local security authority subsystem (lsass.exe) |
| d4f940ab-401b-4efc-aadc-ad5f3c50688a | Block all Office applications from creating child processes |
| d3e037e1-3eb8-44c8-a917-57927947596d | Block JavaScript or VBScript from launching downloaded executable content |
| 5beb7efe-fd9a-4556-801d-275e5ffc04cc | Block execution of potentially obfuscated scripts |
| 3b576869-a4ec-4529-8536-b80a7769e899 | Block Office applications from creating executable content |
| 26190899-1602-49e8-8b27-eb1d0a1ce869 | Block Office communication application from creating child processes |
| 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B | Block Win32 API calls from Office macro |
| 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c | Block Adobe Reader from creating child processes |
| 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 | Block Office applications from injecting code into other processes |
PowerShell
Note: These commands must all be ran as an Administrator.
Again, we can use the Set-MpPreference commandlet to add attack surface reduction rules. This can be achieved like so –
Set-MpPreference -AttackSurfaceReductionRules_Ids RULE_GUID(S) -AttackSurfaceReductionRules_Actions Enabled
As with Group Policy, the action can either be enabled (i.e. the friendly description for the given rule will be enforced), or AuditMode, which will generate an event.
Therefore, to make adding the above rules easier, I have included the above command with each GUID to assist with copying and pasting (hopefully on a test machine!)
Set-MpPreference -AttackSurfaceReductionRules_Idsbe9ba2d9-53ea-4cdc-84e5-9b1eeee46550,b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4,9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2,d4f940ab-401b-4efc-aadc-ad5f3c50688a,d3e037e1-3eb8-44c8-a917-57927947596d,5beb7efe-fd9a-4556-801d-275e5ffc04cc,3b576869-a4ec-4529-8536-b80a7769e899,26190899-1602-49e8-8b27-eb1d0a1ce869,92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B,7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c,75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 -AttackSurfaceReductionRules_Actions Enabled Summary
Hopefully this article has given you some further insight into what Windows Defender can offer your environment. Personally, I never really considered Windows Defender to be much of a contender in the anti-virus market, but uncovering all of this information has really changed my mind.
I must include a massive shoutout to SwiftOnSecurity on Twitter – they gave me the inspiration to look more into Defender and its defence capabilities, and of course a shoutout to the Microsoft Security team for their dedication to their products and their receptiveness to community feedback.